In the greater scheme of things, login warning banners exist to fulfil control requirements. They exist to support the legal process that will say “there was a warning, you still proceeded”. They superseded the old “Welcome…..” system messages which [allegedly] led to a hacker being acquitted in a legal case.
The requirement still exists – see the NIST 800-53 AC-8: System Use Notification
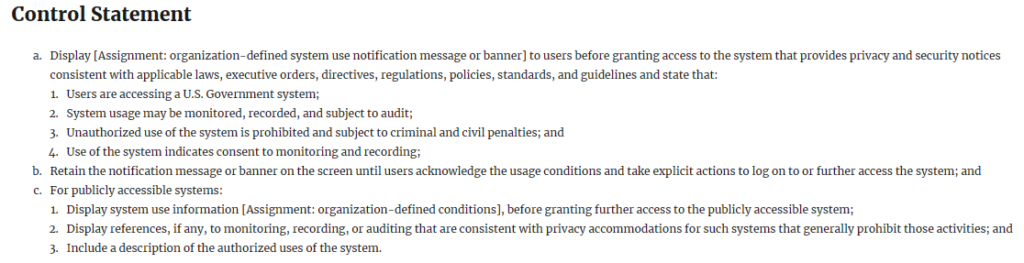
As a CYA control, it exists. The expectation is any “good” hacker will ignore the warning and any semi-legitimate user of a system is already bound by contractual terms. So a box-checking exercise, in the end, to support other stronger controls.
Of course this leads to a context in which the OpenCanary joins the banner game. Clearly, the intention is to poke and prod any person or thing trying to log in while also assuming they will not read nor care about the banner.
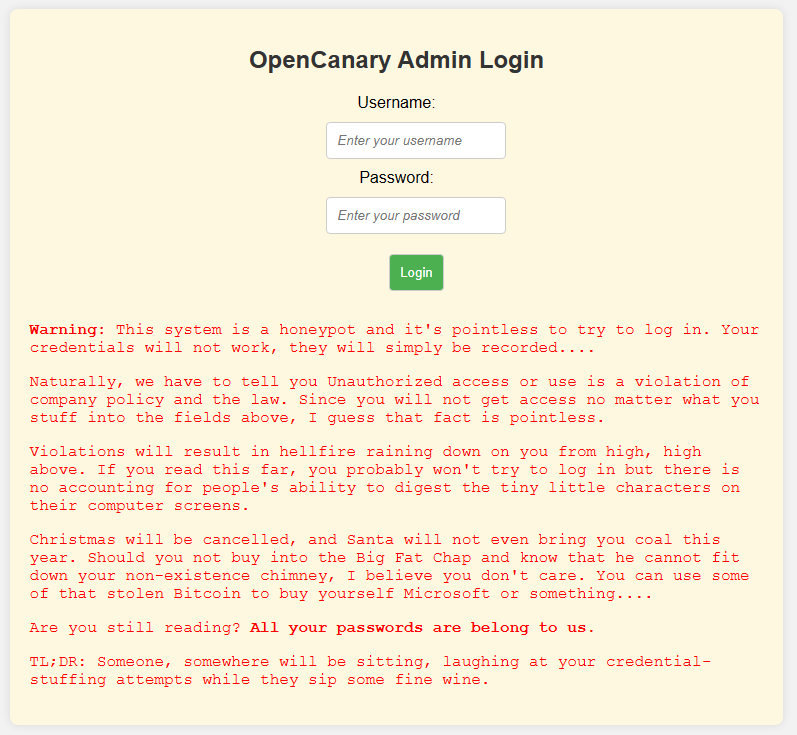
There can be no suggestion that this warning banner is anything but transparent with a healthy dose of geek humour. To be fair, not many login attempts happen on the HTTP layer of the honeypot but it’s out there, waiting to be found and read!