Goodbye OpenVPN, hello Wireguard!
But I am keeping you, Tailscale!
I’ve long been leveraging OpenVPN on a Synology unit to allow VPN connectivity into my home network but, with the home now sporting two PiHoles, it seemed right to dig into PiVPN.
Given that I have a virtualised Ubuntu server (or three) running PiHole, it seemed a perfect fit to install PiVPN onto one of the hosts.
Installation is text-based but very straightforward, the install process is well thought-out and logical with defaults towards the best posture. Wireguard is installed by default, OpenVPN not.
It does of course detect and use the PiHole which means my devices, even when off-net benefit from being able to:
- Use PiHole and avoid adverts
- Leverage my SmartDNS functionality allowing region change for some entertainment providers
- Have a most awesome Wireguard function on MacOS and iOS/iPadOS for on-demand connectivity
- Let my MacBook run Time Machine backups while I am off the network (bye-bye flaky Tailscale implementation on Synology NAS….)
The heavy lifting? Opening a port on my router to allow the UDP traffic in (actually in my case, two routers…..go figure). I already have a DNS entry for my home IP address and so that is easy to add to the configurations.
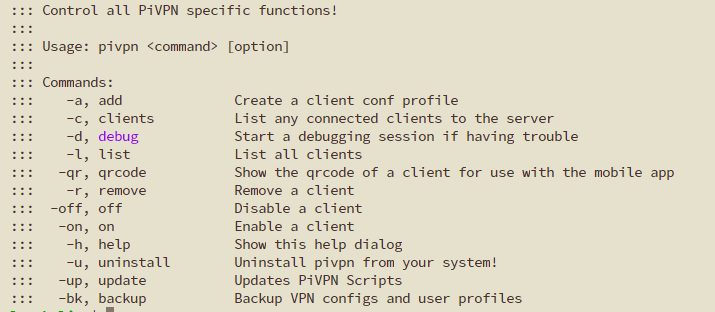
Adding Devices
Adding a device (there is little concept of users in Wireguard, rather devices) is simple:
pivpn -a
You name your device and the magic is done. You just need then to add the configuration to your device (I would recommend creating a client configuration per device).
Mobile devices are the easiest to add. Add the QR code option to the command and you choose a number:
pivpn -qr
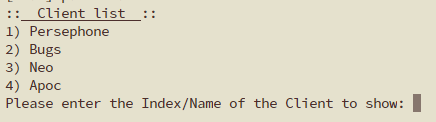
This will result in a QR code being displayed and a phone or tablet Wireguard App will then ingest the configuration and you can adjust it. Since my PiVPN wants to put my public IP address into the connection details, I have to overwrite that with my DNS entry.
MacOS and Windows devices can also be configured easily; I found outputting the conf file to the screen and copying it into a file for the client on the devices works best. It’s quick and easy.
Caveats and Observations
- Windows does not have an on-demand mode at this time (on the winget-sourced Wireguard.Wireguard package).
- I run Tailscale and Wireshark at the same time on my devices; Windows seemed to not like routing Tailscale via the Wireguard tunnel and needed “block untunnelled traffic” unchecking. Yes, it then becomes leaky but my Windows machine is not often on the move. MacOS does not have this issue.
All-in-all, for about an hour’s work across my devices, it’s brilliant. It has replaced my remote backup to TimeMachine via Tailscale that was problematic, I think this is down to hardware limitations on my Synology unit.
PiHole + PiVPN = awesome!