The OpenCanary has been feeding Splunk via WebHook for over a week now and the statistics are becoming clear. More ports, more protocols means more interest from entities scanning the Internet and attempting to get into the box.
First, let’s look at the Popular Ports to see what peaks the Interest:
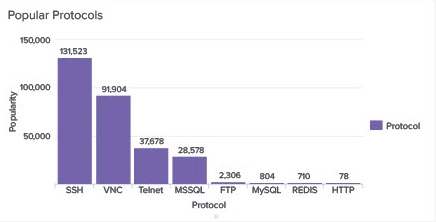
Clearly, the major intent of anyone trying to connect to the box is to take it over with a distant second goal to see if data can be pulled from it. Attackers still believe Telnet is a thing (and it absolutely will be for some)!
A breakdown of some statistics:
- Around 547 connections per hour seek a GUI via VNC (port 5901). These must be the worst of the hackers, wanting to avoid a command line experience…! That would equate to 4.75 million connection attempts per year
- SSH is extremely popular on port 22; 782 connection attempts per hour, thus likely around 6.8 million per year
- Telnet is still a port that gets probed 224 times per hour on average and up to 2 million times per year
The volume of passwords shared to the OpenCanary excludes any attempt with a pre-shared secret on the VNC port.
The login attempts are extremely frequent and there are a bucketload of passwords, some more common than others.
- The OpenCanary receives, on average, 549 passwords per minute
- This would likely be around 4.8 million passwords per year
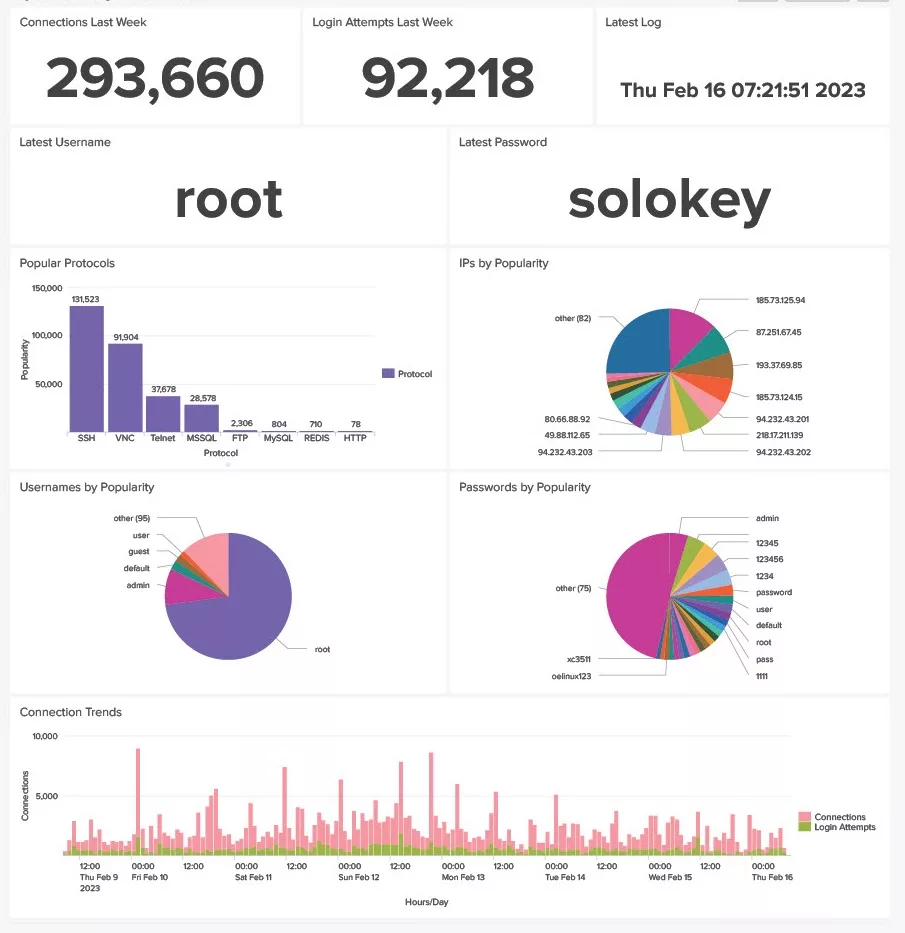
This is all being fed into a Splunk Enterprise platform running on linux with the OpenCanary sending WebHooks via a Tailscale layer. This is what a week of logs looks like in Splunk terms:
- Around 300’000 events per week in the OpenCanary index, as seen above; that would be 15.6 million events per year
- 120Mb storage or 6.2Gb per year
I have of course built a dashboard (three, actually – for week, month and year overviews). The upper values in the week dashboard update regularly, making it interesting for the viewer. Counts and login values change within the minutes to reflect the feed coming into Splunk.
A Canary, either commercially from Thinkst or using the OpenCanary project, makes a lot of sense both at the perimeter or sitting in a network. While this is my most interesting OpenCanary, it is not my only one; I have one in my DMZ and one in my network, functioning just to let me know if someone is knocking on my door somewhere, somehow.