
101 Things to do with Tailscale
#1: Send 5.5 million webhooks to Splunk per month Things One, Two and Three log all events real-time...
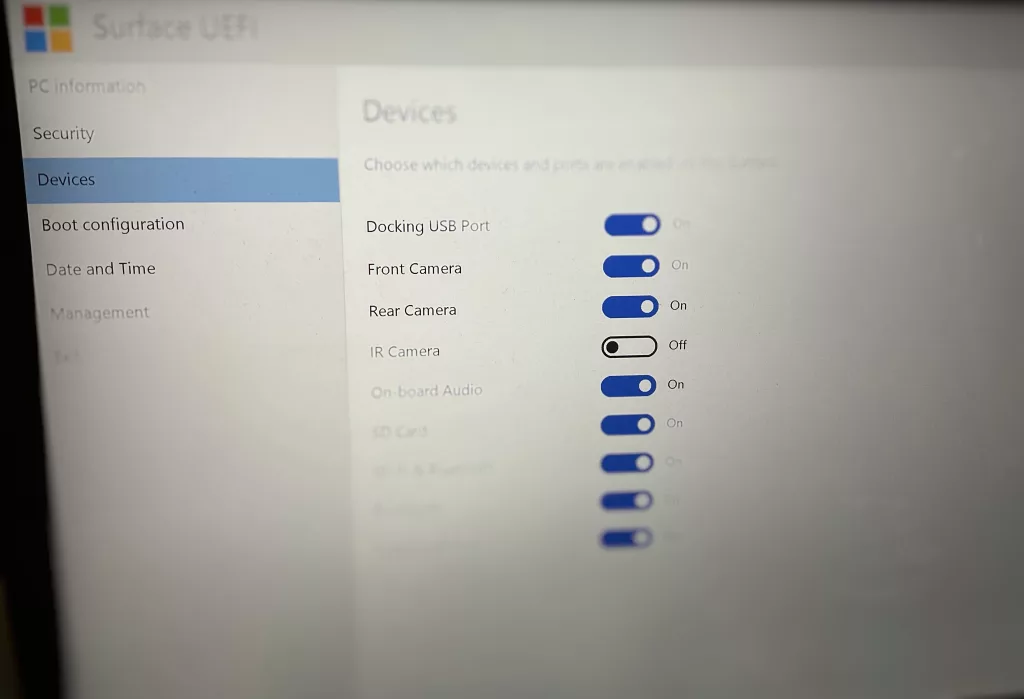
(Yet) More: Solving the Microsoft Surface Pro 7 BSOD
No Blue Screen of Death for me…. It’s been quite some time since I experienced a BSOD on...

Time Machine backups via PiVPN/Wireguard
Time Machine via Tailscale to Synology was not robust enough As a MacBook owner, I like to leverage...
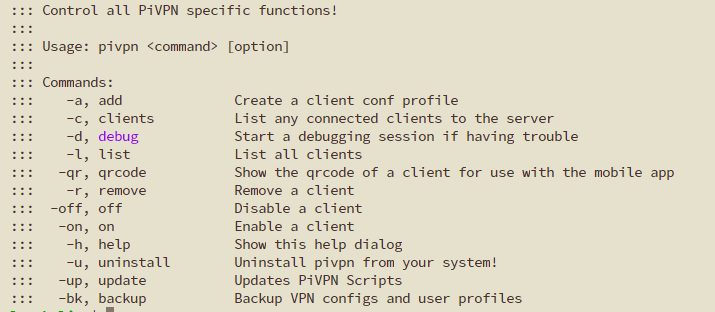
PiVPN – easy, packaged VPN
Goodbye OpenVPN, hello Wireguard! But I am keeping you, Tailscale! I’ve long been leveraging OpenVPN on a Synology...
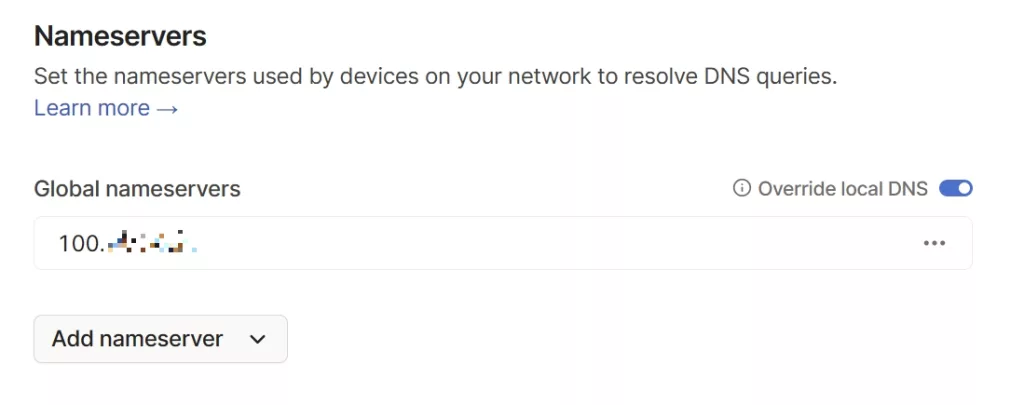
The pihole in the sky – now with Tailscale
Blocking Everywhere Building on the idea to have a pihole in the sky, having a Pihole that I...
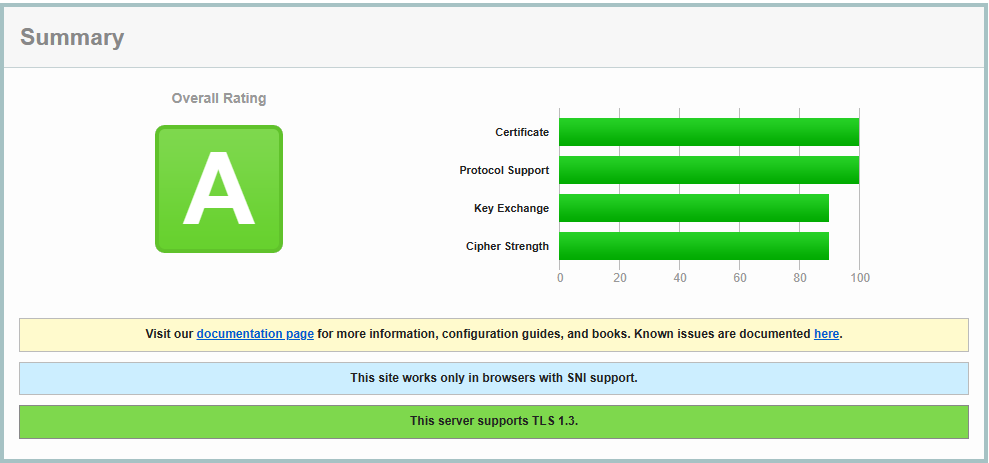
Caddy + Tailscale + Synology = Happiness
The discovery during looking to make Lighttpd run over TLS led me to find Caddy. It’s a TLS-first...

Sony, Quad9 and Barbara Streisand
Everybody probably has heard of the Streisand Effect. Perhaps everyone except Sony Music Entertainment Germany, that is. A...
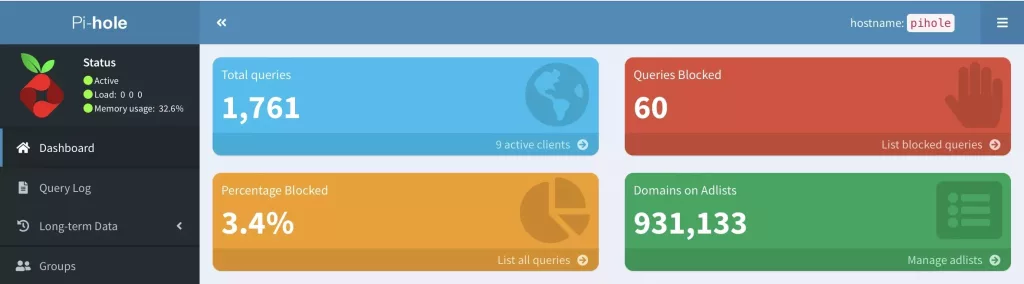
The pihole in the sky
Pihole. it‘s brilliant. It kills ads and tracking – dead. The server deploys in 5 minutes and offers...
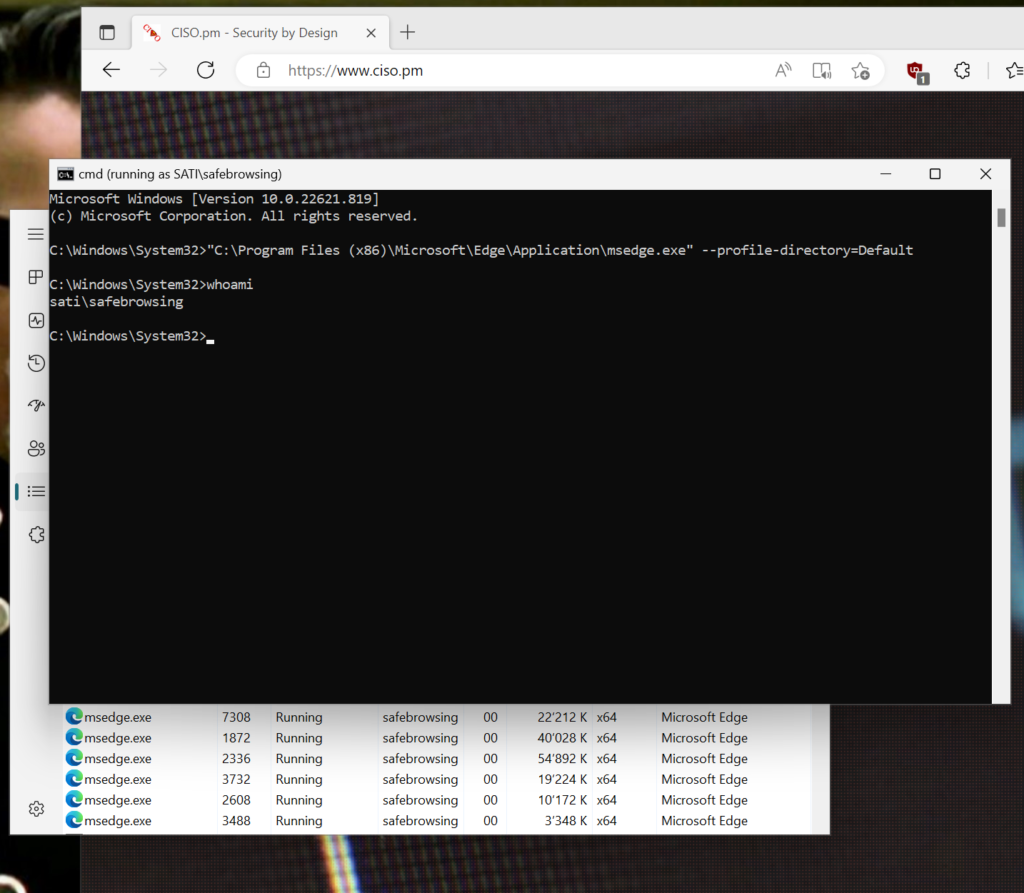
Browser Isolation: Running a browser as another user
The notion of separating the user context from the browser (and possibly the email client) is not new;...
Solving the BSOD on a Microsoft Surface Pro 7, Part 2
Because Part 1 did not solve it! It’s been years since the BSODs started on my Surface. It...